Azure VMware Solution: A comprehensive guide to LDAPS identity integration - Part 4
Jan. 25, 2023Author(s): Robin Heringa and Fletcher Kelly
Implementing LDAPS identity integration with Azure VMware Solution series - 4 of 4
This is the fourth and final part of the blog series on how to implement LDAPS identity integration with Azure VMware Solution. Other parts of this series can be found here:
These steps, for now, are run manually from the Azure Portal. This will be found “Azure VMware Solution” and under Operations, Run command. Then select “New-LDAPSIdentitySource”. An automated way of executing the run-command is in the making. Please check back soon as this article will be updated as soon as this is available. Navigate to Azure Portal and ensure you are on AVS Private Cloud blade
- In the AVS Private Cloud blade, click “Run Command”;
- Ensure Packages is selected.
- Click “New-LDAPSIdentitySource”.
- Ensure the correct Run is open before populating the required information.
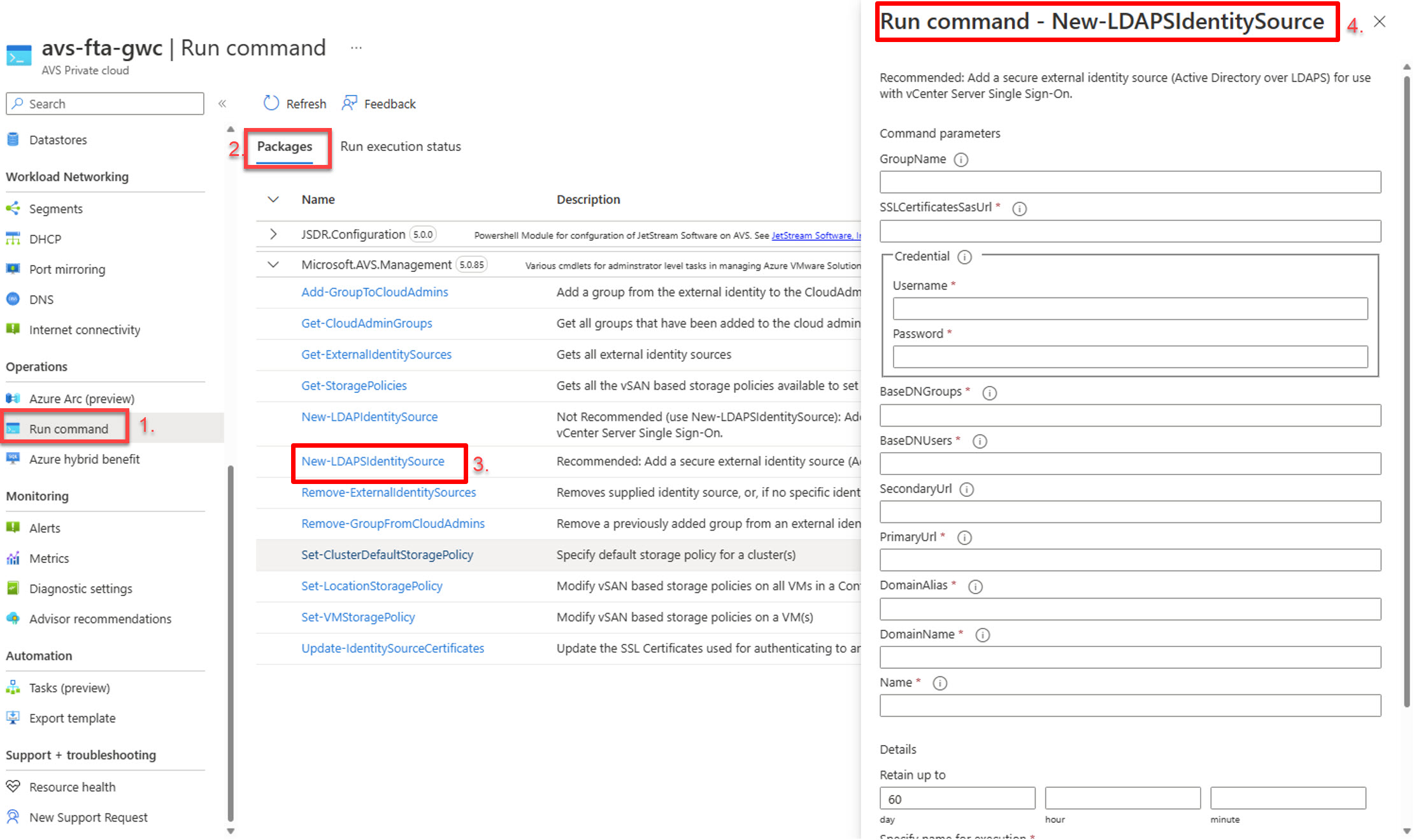
Populate the information as needed.
The SSLCertificateSasUrl is a single string consisting of the SASTokens separated with a “,”. For example:
https://avsgwcsa14a2c2da.blob.core.windows.net/ldaps-blog-post/avs-gwc-dc001.cer?sv=2021-10-04&st=2023-01-12T13%3A46%3A45Z&se=2023-01-13T13%3A46%3A45Z&sr=b&sp=rwd&[Removed],https://avsgwcsa14a2c2da.blob.core.windows.net/ldaps-blog-post/avs-gwc-dc002.cer?sv=2021-10-04&st=2023-01-12T13%3A46%3A45Z&se=2023-01-13T13%3A46%3A45Z&sr=b&sp=rwd&[Removed]
Example string:
https://avsgwcsa14a2c2da.blob.core.windows.net/ldaps-blog-post/avs-gwc-dc001.cer?sv=2021-10-04&st=2023-01-12T13%3A46%3A45Z&se=2023-01-13T13%3A46%3A45Z&sr=b&sp=rwd&[Removed],https://avsgwcsa14a2c2da.blob.core.windows.net/ldaps-blog-post/avs-gwc-dc002.cer?sv=2021-10-04&st=2023-01-12T13%3A46%3A45Z&se=2023-01-13T13%3A46%3A45Z&sr=b&sp=rwd&[Removed]The other values would need to be updated as per your environment. The BaseDNGroups and BaseDNUsers are the Distinguished Names for the groups and users. These can be found using the ADSIedit tool and navigating to the required groups within Active Directory and noting down these values. More information can be here about Distinguished Names
With the BaseDNGroups and BaseDNUsers, watch the values used as these should be under the same tree. In this example, “OU=Corp,DC=avsemea,DC=com”
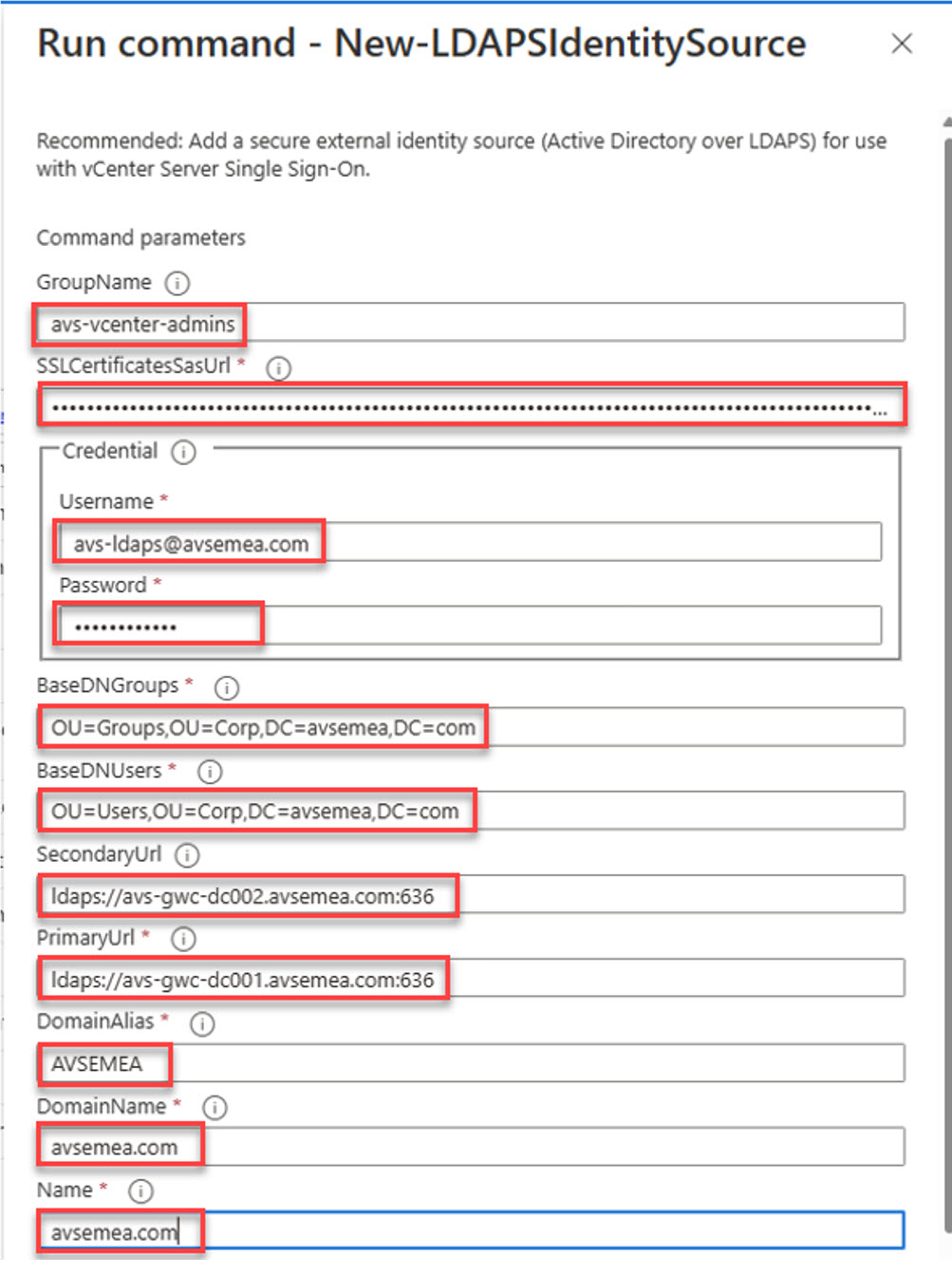
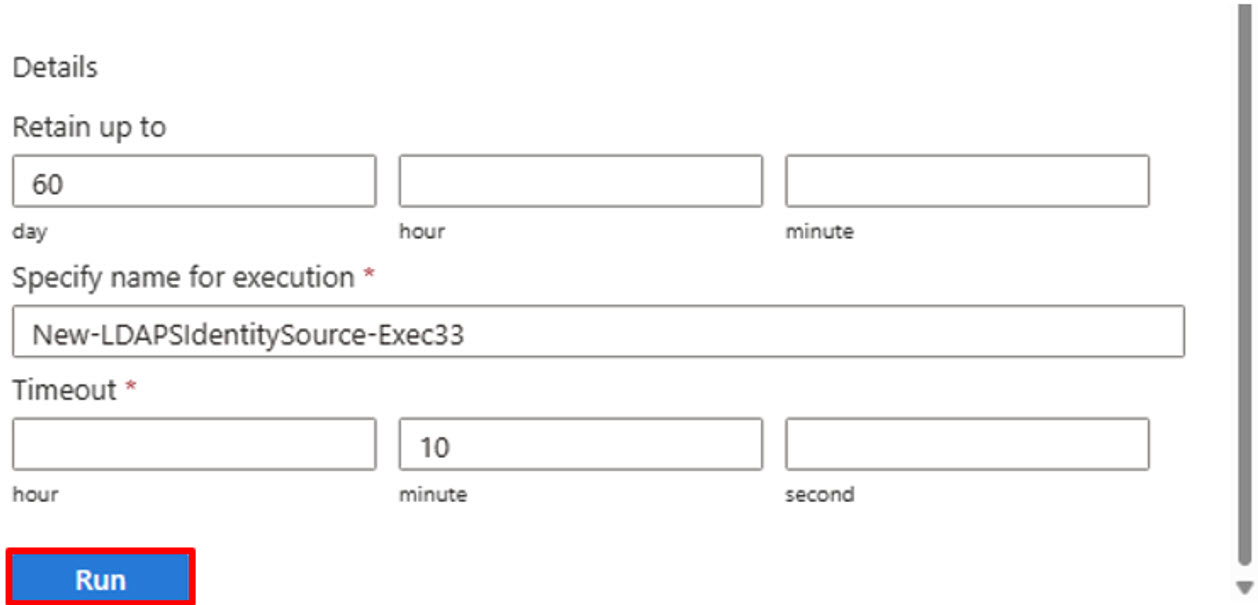
Once all information is entered, Run the command. You can check the status of the Run command within the portal. Navigate to Azure Portal and ensure you are on AVS Private Cloud blade
- In the AVS Private Cloud blade, click “Run Command”;
- Ensure “Run execution status” is selected.
- Click the latest run execution that is applicable to your environment. In this case, New-LDAPSIdentitySource-Exec33.
- Ensure you click the Execution name (3.) that is the running state.
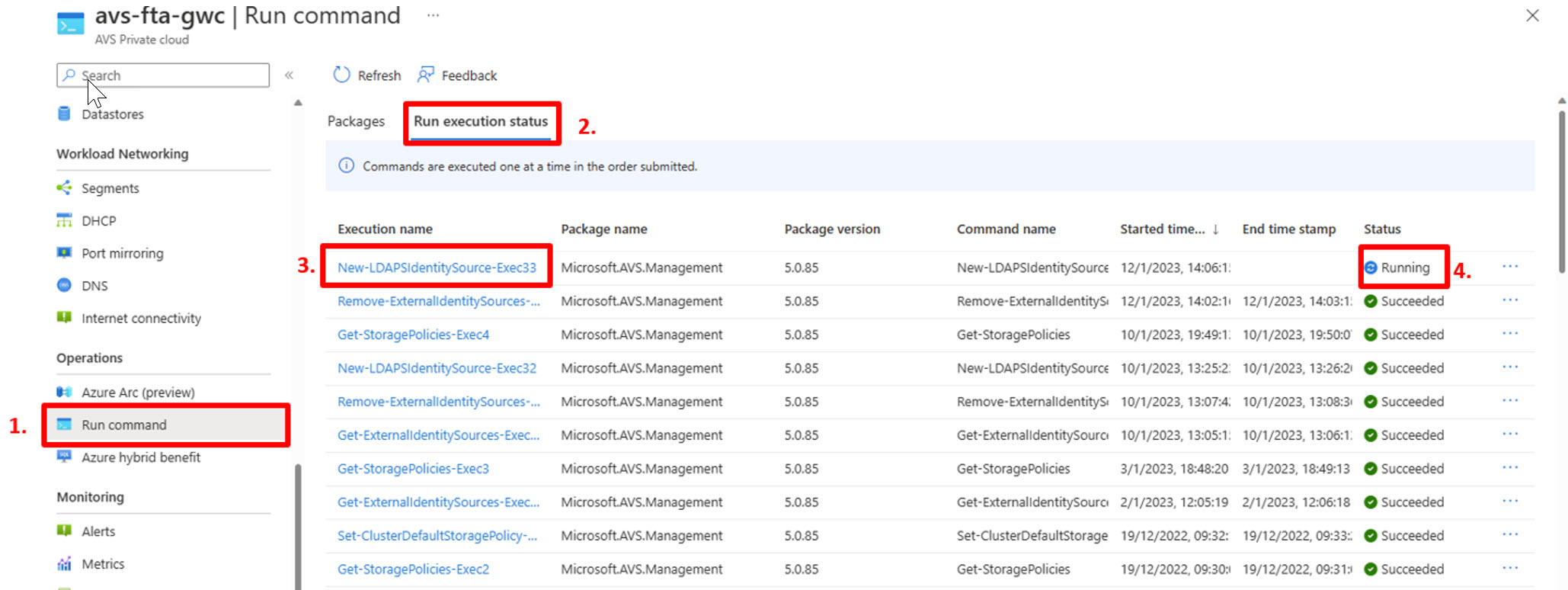
You can check the status of the job now and you are waiting for all the tasks to be completed and show that your selected group was added to CloudAdmins Once you have clicked the Execution name link
- Check the information tab to see the steps being executed by the script;
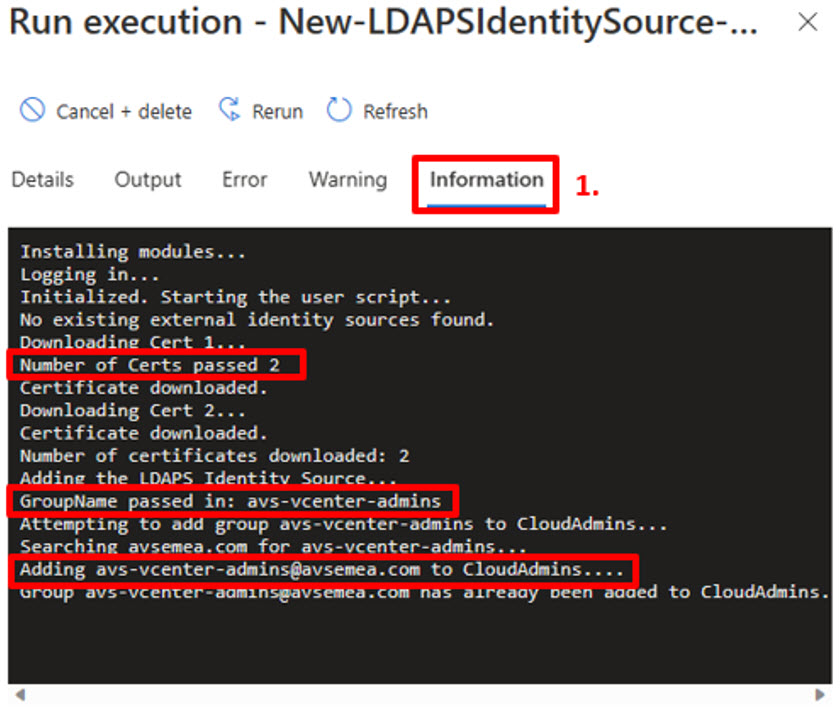
You can also check the output and ensure that the correct name was added. Once you have clicked the Execution name link
- Check the Output tab to see the steps being executed by the script;
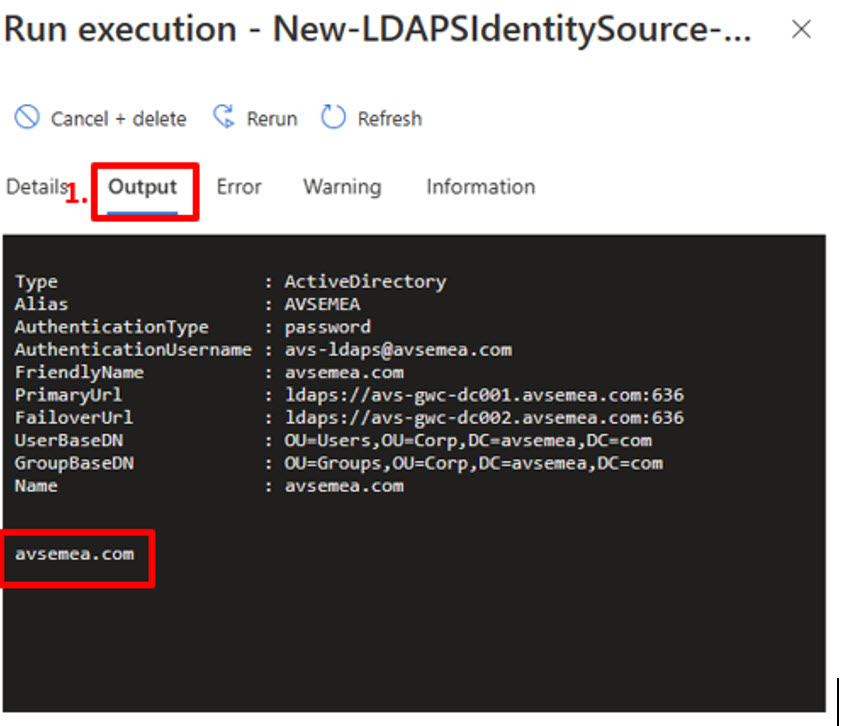
You can log on with LDAP based credentials. Using the link found under “VMware credentials”, navigate to vCenter Server Credentials Web client URL Navigate to Azure Portal and ensure you are on AVS Private Cloud blade
- In the AVS Private Cloud blade, click “VMware credentials”;
- Click the copy icon for the WebClient URL under “vCenter Server credentials”
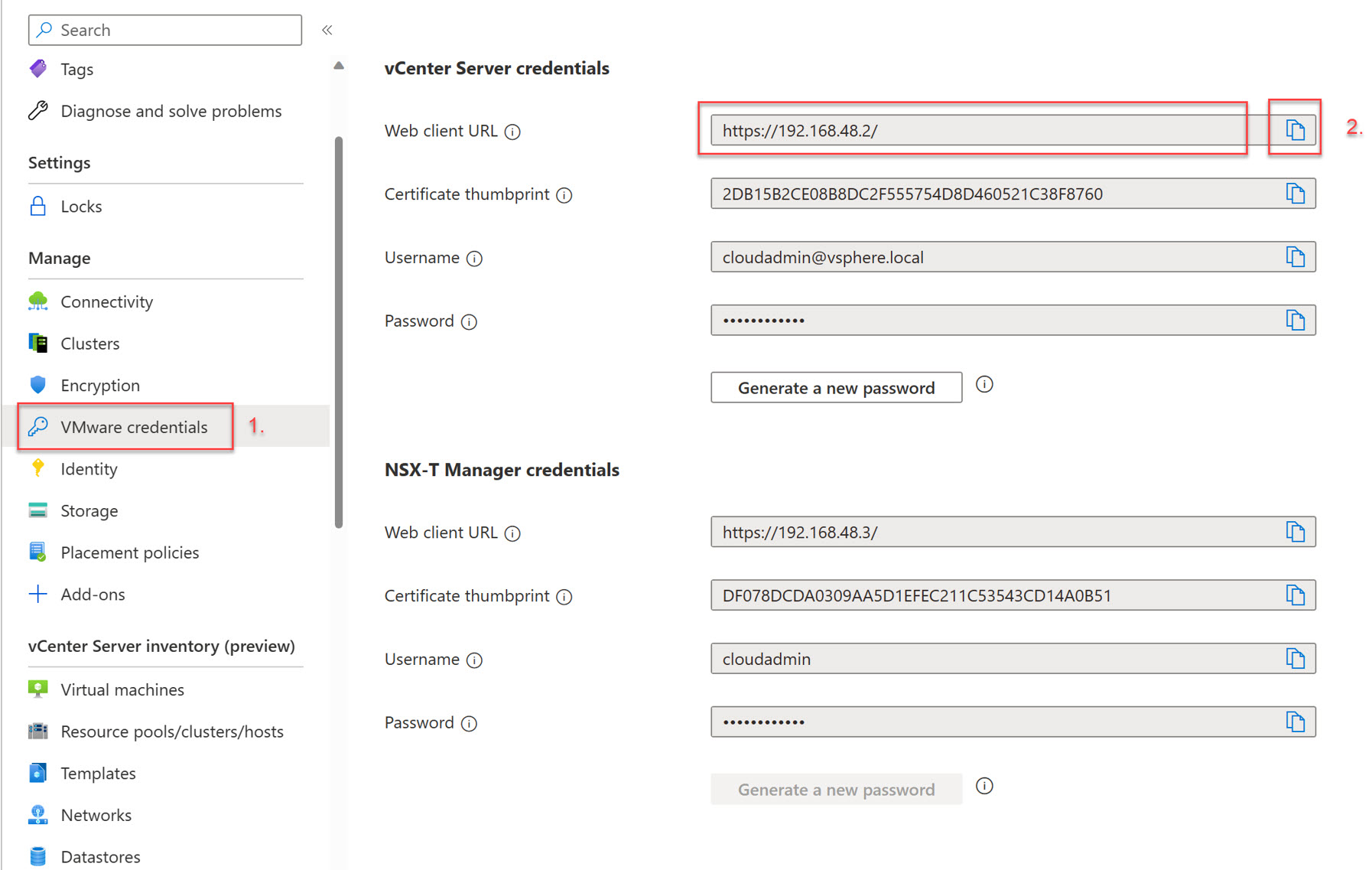
Navigate to the URL with your browser of choice and use your Directory Services based credentials to ensure that login and authentication is working as expected.

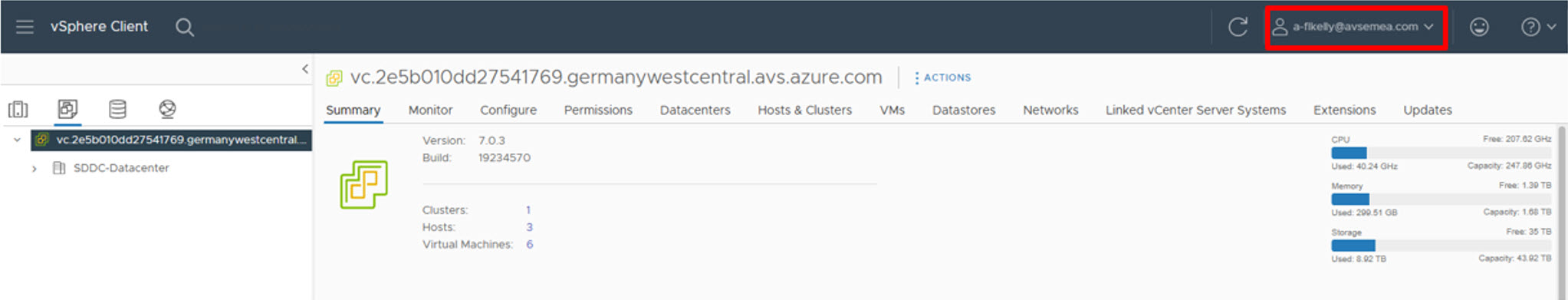
Logon to Azure VMware Solution based components is now possible and should be now be working as expected.